CloudFlow Secure Tunnel
Distributed systems often run across private & multiple cloud provider networks. As your workload runs in various locations around the world and moving as traffic changes, it may need to connect to databases and APIs that are protected within the networks of other cloud providers or datacenters. Because of the dynamic nature of these networks, secure, encrypted tunnels are used to allow such connections to be made. The CloudFlow Secure Tunnel is a way to solve this problem with proven technology.
This guide explains how to use the CloudFlow Secure Tunnel in a popular configuration, enabling access to a database in AWS RDS. You will likely be able to apply the container directly to a wide variety of situations beyond the one described here. The source code is available in CloudFlow GitHub as needed.
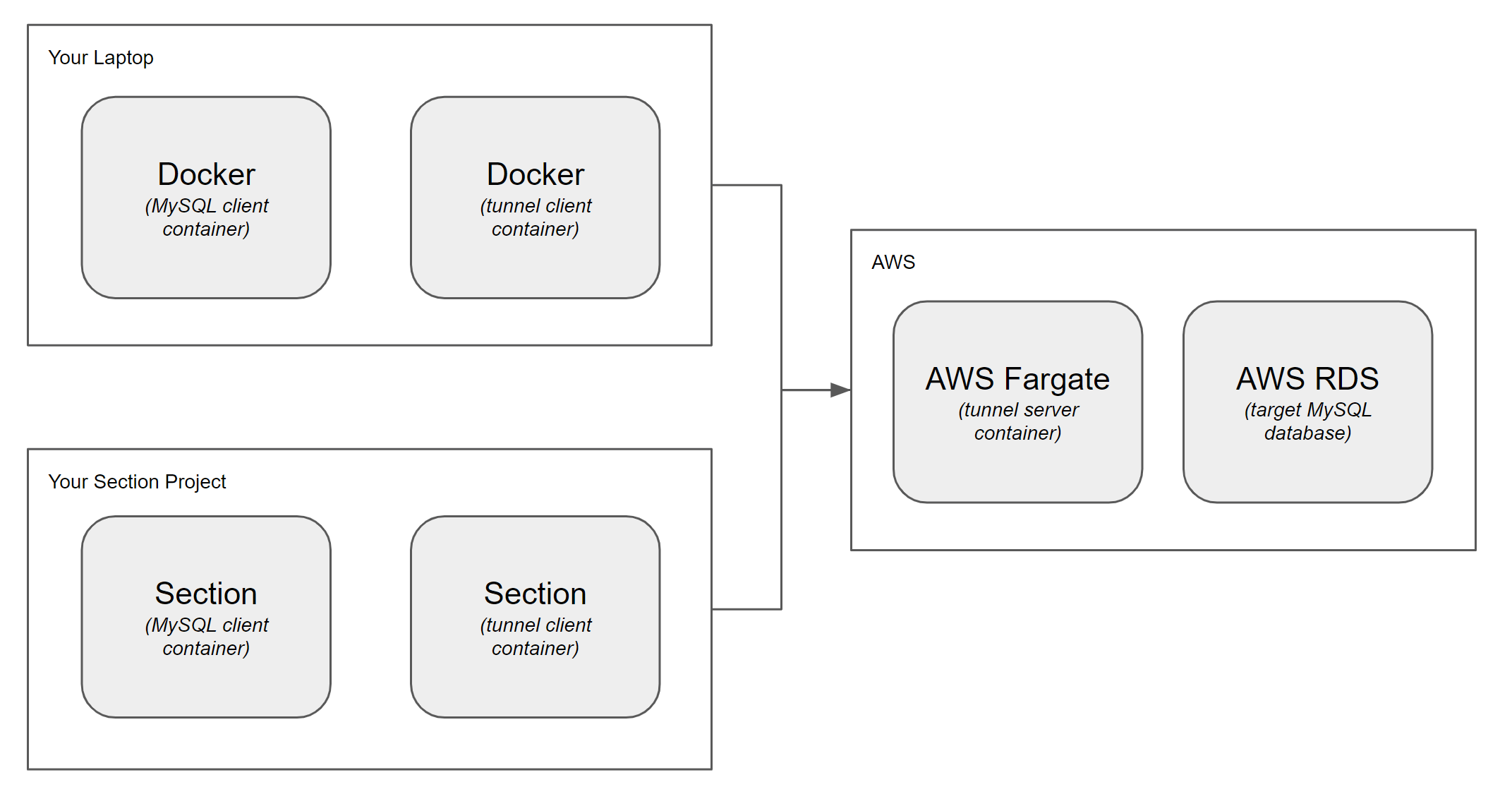
The two articles in this guide help you setup three components of an example tunnel.
- You will first setup a target on AWS, which is the tunnel server side. The target database will be AWS RDS, and the AWS Fargate serverless container hosting service will be used to host the CloudFlow Secure Tunnel server container.
- The AWS guide will then proceed to use Docker from your laptop to establish and test a client connection to the server.
- Then in the second guide you will deploy the CloudFlow Secure Tunnel to a CloudFlow Project, and test the connection to your RDS database from there.
The Docker example won't be needed in production but is provided as an experimental stepping stone.
You can use the server capability of CloudFlow Secure Tunnel to gain access to other targets, such as Azure, GCP, and more, by running the container on their corresponding container hosting services and pointing to their databases.